The Right Time for a Cybersecurity Threat Assessment
Keeping on top of the security needs of your organisation can be difficult, especially in times of increased growth and business change and when internal resources are limited. Knowing when to ask for help and when to invest in the big picture of your cybersecurity stance is a decision every CISO(?) needs to make.
Typically, the time to have a cybersecurity assessment is before exposure or an incident happens, but there are several reasons that make now the right time.
You need to comply with regulations such as NIST, MITRE and ISO
You’ve never had a second opinion on cybersecurity
You need to verify and prove your security posture to your customers
You need oversight over an increasing third party supply chain
Your organisation has recently been the victim of a cyberattack
You’re wondering if you have gaps in your security posture
Whether your goal is compliance, validation that your stance is robust, or you’re considering outsourcing part of or even all of the cybersecurity function of your business, a cybersecurity assessment can help you get a detailed, measurable overview and set out what you need to do next to manage cyber risk and protect your organisation’s reputation. Even organisations that have a relatively mature security model in place may decide that they need an external view of their structure and risk profile so that any gaps or priorities can be identified and addressed.
- 7% Of CISO's said x
- 3 Fact about number of Apto Customers
- 100 Clients agree with x stance
Multi-Step Cybersecurity Discovery Process
Apto’s discovery assessment process will be completely customised to meet your goals for compliance, confidence or validation of your security posture. We’ll take the time to really understand your organisation and where it currently stands and help you decide where to go next.
Threat assessments require a significant amount of collaboration with many parts of your organisation as it will include a review of your non-technical and technical security policies, so we actively encourage engagement from a wide range of stakeholders.
We’ll guide you through a process that has 12 methodical phases that encompass data discovery, analysis of threats, report preparation, and review.
Phase 1: Consultation & Access
Phase 2: Data Collection & Analysis
Phase 3: Report Preparation
Phase 4: Delivery, Review & Next Steps
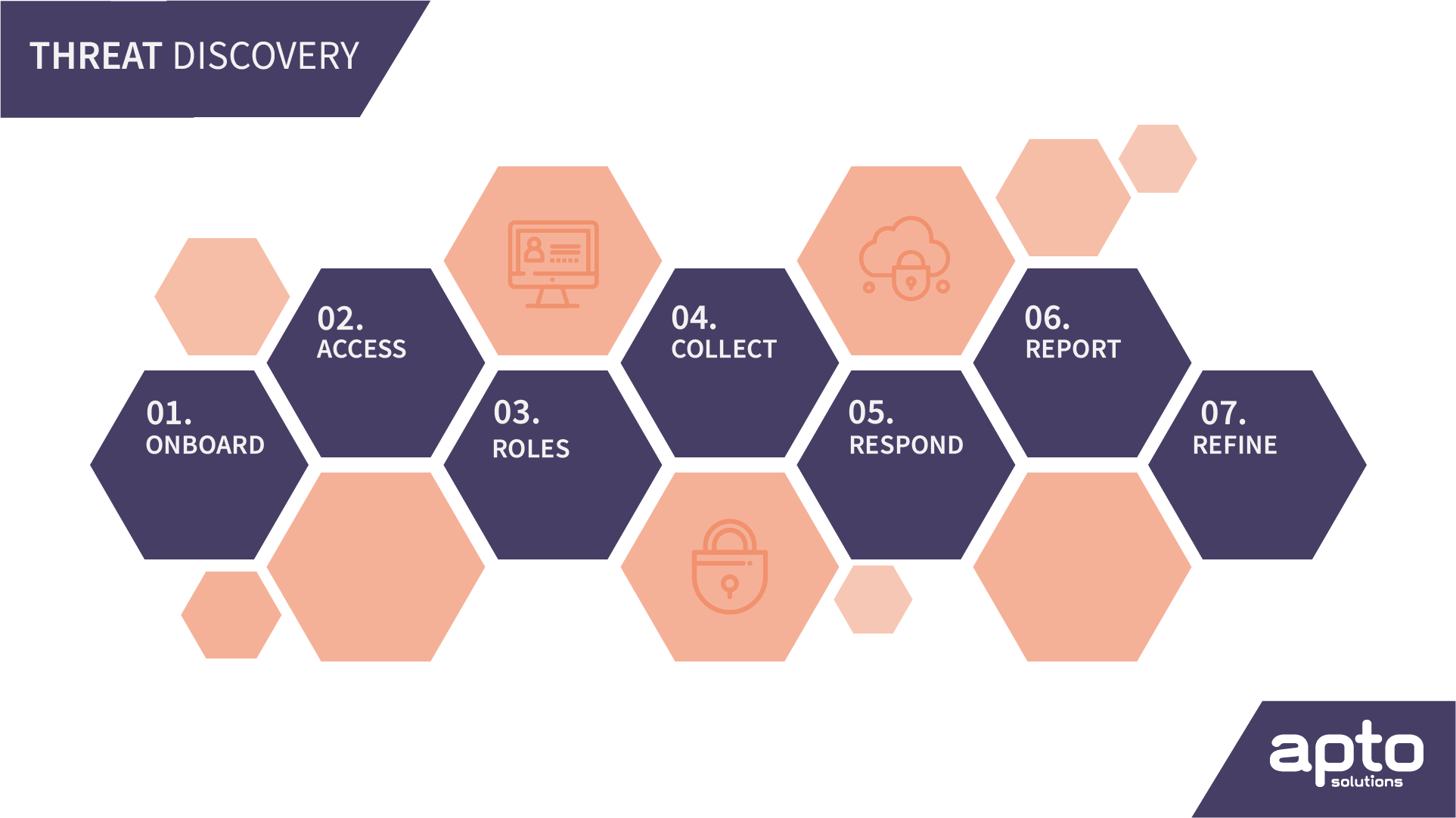
Scope of Apto Discovery
As part of a typical 10-day consultation process, we will perform a comprehensive review of the following areas: (What does this look like, this should be a long list covering everything in clear language)
- Consultation with stakeholders across all parts of the organisation
- Identify the industry-specific key security challenges
- Existing operating/threat model
- Risk/governance/compliance/ tools/policies
- Assess TDIR
- GAP analysis
- Tooling Recommendation
- Use Case Mapping
- etc…
Examples of detailed scope (Are these more security assessment focused?)
- Network Architecture and Protections
- Server Environment & Workstation Management
- Inbound Firewall Configurations
- Outbound Firewall Configurations
- Evaluate the Effectiveness of Patch Management Tools
- Evaluate Antivirus and Anti‐Spyware Tools
- Shared Permissions Review
- Internal Vulnerability Scan
- Security Policy Assessment
- Backup, Restoration, and Disaster Recovery Planning
What Our Customers Say
{insert customer testimonial or client or influencer quote]
Why Apto for Cybersecurity Advisory & Assessments?
Tailored To Your Organisation
Apto is a small but dedicated team of industry experts with over xx years of experience. We aim to truly understand your organisation at a deep level and put your business objectives and industry-specific needs at the core of what we do. We consider your company culture, size, risk tolerance, complexity and what you are trying to implement and maintain. This ensures that the work you receive from us is specific and focused on your organisation.
Actionable and Reliable
Our tailored approach ensures that the deliverables and outputs from the discovery process are appropriate, actionable and focused on the threat landscape you will be exposed to. The final report from this process will allow you and your organisation to fully understand what’s next for your cybersecurity posture and where to focus resources best so you know how to define, design, build, implement and operate your security architecture into the future.
Platform And Service Independent
Although Apto
About Apto
Brief company history and list of accreditations.
