
Hello! Welcome to our coverage of the second day of Splunk .conf24. Today’s keynote was really packed with updates around Splunk Cisco integrations and enhanced product announcements. Here’s a detailed recap of the major highlights and takeaways from the kick-off of this year’s event. Main takeaways are more CISCO product integrations, improved ingest capabilities, federated data searching and ES Security improvements.
Clear Product Vision
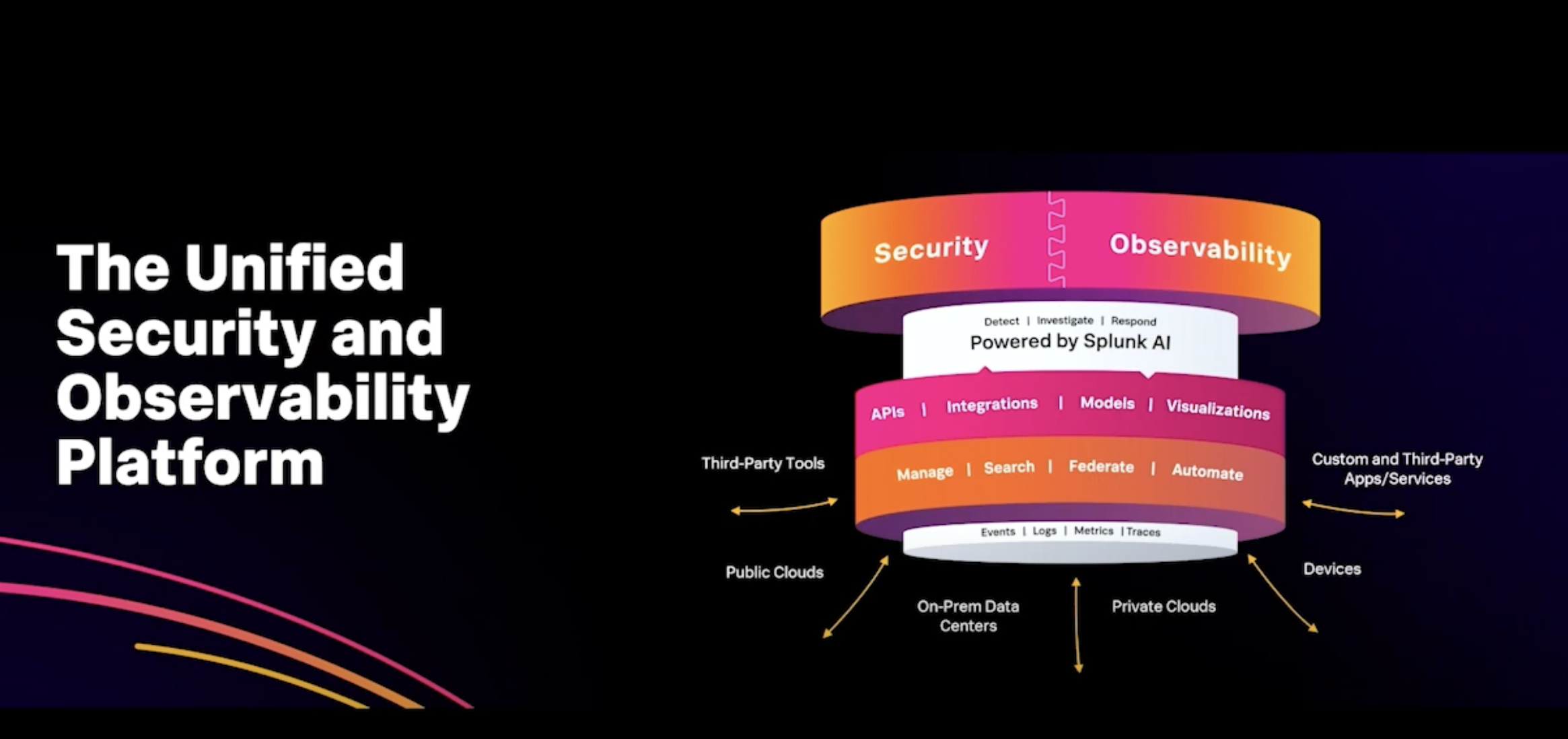
A key message was Splunk’s mission to provide Visibility and insights across your entire digital footprint powering actions that improve security reliability and innovation velocity. This is both leveraging the increased visibility that the Cisco products provide, while also collecting the intel from the entire digital foot print.
It’s not just about managing the applications the devices, the infrastructure, it’s also about reaching into the networks, endpoints, cloud services that you use as well and understanding all of that lateral movement in your network it occurs within a network. Some of the product integrations below greatly increase this functionality.
Product Integrations
Several significant product integrations were announced for Splunk, such as:
– Splunk and Talos – Talos (threat intelligence) processes about 550 billion security events daily that will enrich Splunk with Talos data across the entirety of the Splunk.
– Splunk and Thousand Eyes – enriching Splunk with vast network intelligence data
– Splunk Enterprise and CISCO XDR – Filter telemetry high fidelity low volume into SIEM with CISCO XDR will correlate alerts to a high level alert for SIEM ingestion. Talk about full loop of learning from the threat intelligence gained in the SOC and then enrich those detections lower in the stack.
– Splunk and HyperShield – better signalling from a distributed fabric with improved detection, having the ability to push more action down, so you can do things like quarantine and snapshot earlier.
Unified Data Ingestion
Mentioned yesterday briefly the detail is now revealed !

The ability to ingest data once, metrics, events logs and soon after traces directly into Splunk. Feed that into Enterprise security and the Splunk observability Cloud. Make it available to ITSI and in the future app Dynamics as well as enriching it with signals from the Security Suite and from Thousand Eyes integrating with those products in flow. This means broader visibility across everything in the SOC and NOC and IT operations as well and plus routing that data not only to Splunks applications and services but also e.g Data Lakes.
Data Management and Federation

With new data management and Federation capabilities it will provide the choice and end to end control of data everything from ingest to filtering masking routing as well as search and analytics. Data management and Federation are two pillars that go hand in hand, there is no full control with just one.
It’s not enough to shape and Route data if it can’t comprehensively search it. Splunk continue to invest in data management with the ability to create and manage pipelines that are powered by spl2 so that one can filter mask and route data. Last year Splunk released Edge processor which allows you to deploy these pipelines at your network Edge and this gives you greater control over data such as PII.
Ingest Processor
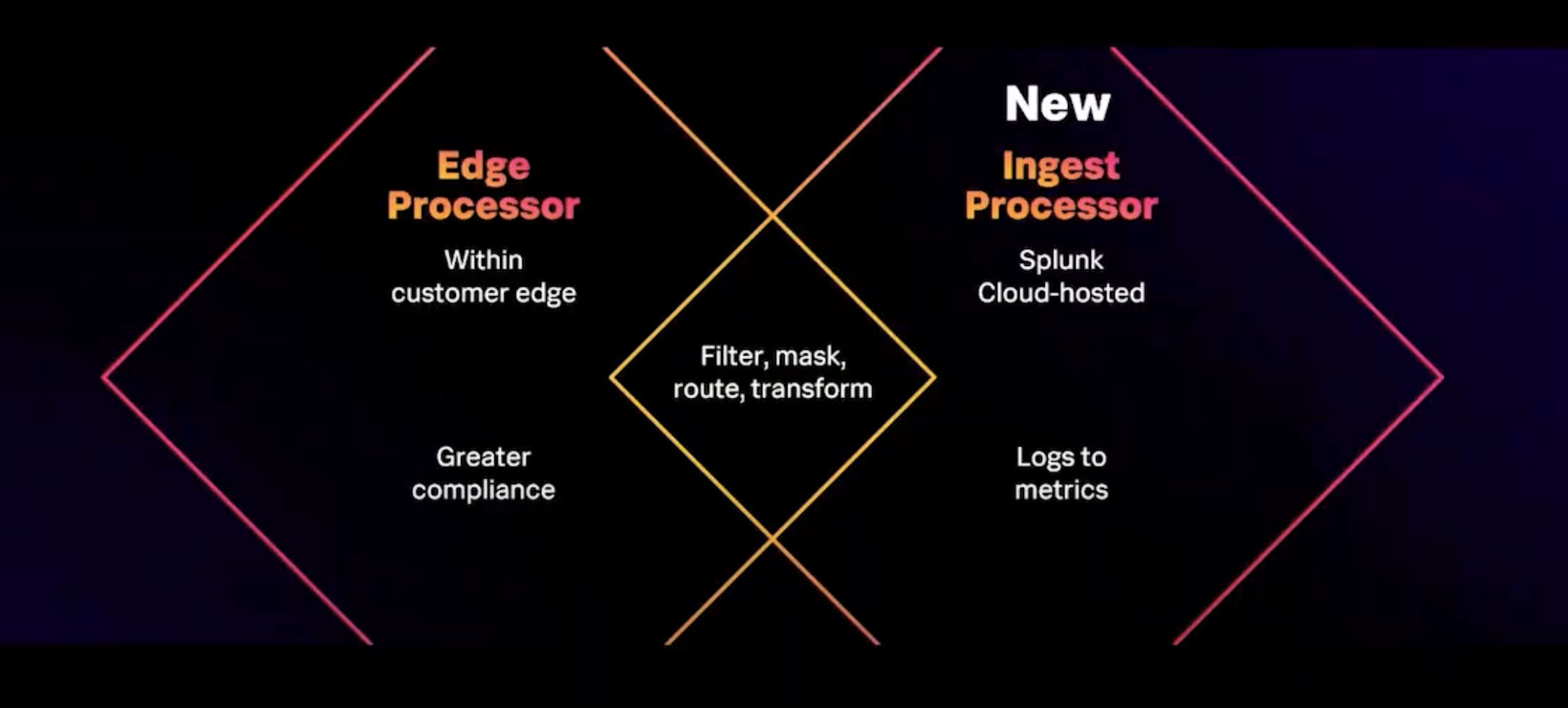
The new Ingest Processor offers more choice in where you deploy those pipelines and includes the ability to convert logs to metrics and route them to the realtime metrics backend, to support observability and security use cases.
Federated analytics; last year Splunk released Federated search so that you can remotely search S3 data from Splunk and correlated with your Splunk data. This was a solution for historical and audit use cases, now with Federated analytics starting with Amazon Security Lake you can selectively fetch data from the Security Lake and build it into a short-term index and this enables higher performance use cases like monitoring and ad hoc investigations.
Asset and Risk Intelligence
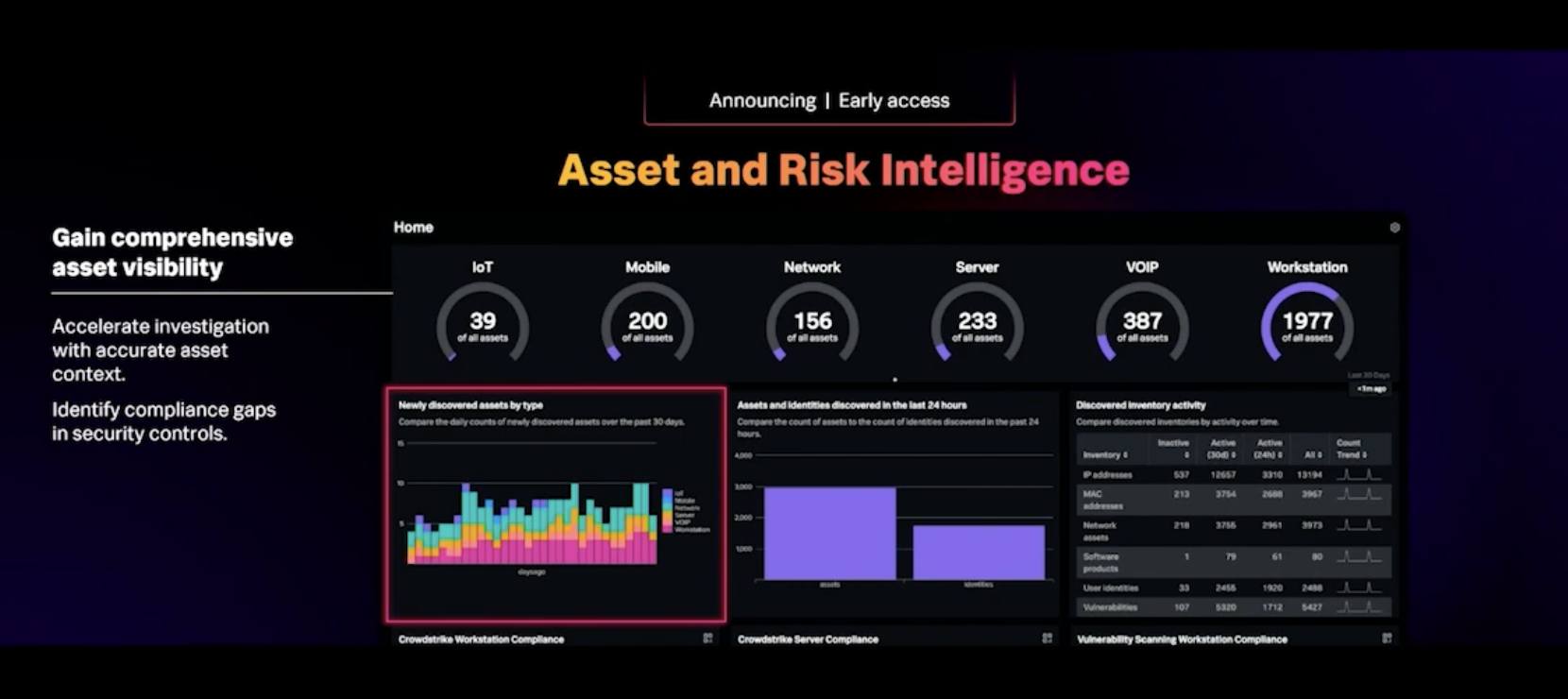
ARRI (launched at RSA last month) for short, will discover items, devices, users automatically from the data sources that are probably already being sent to Splunk and once discovered, these assets will integrate those and will synchronise with things like Enterprise security asset and identity framework but also with third-party inventories like Service Now cmdb and once an asset’s been discovered it’s continuously updated with new information. This is pretty interesting to explore more.
AI Assistant in Enterprise Security
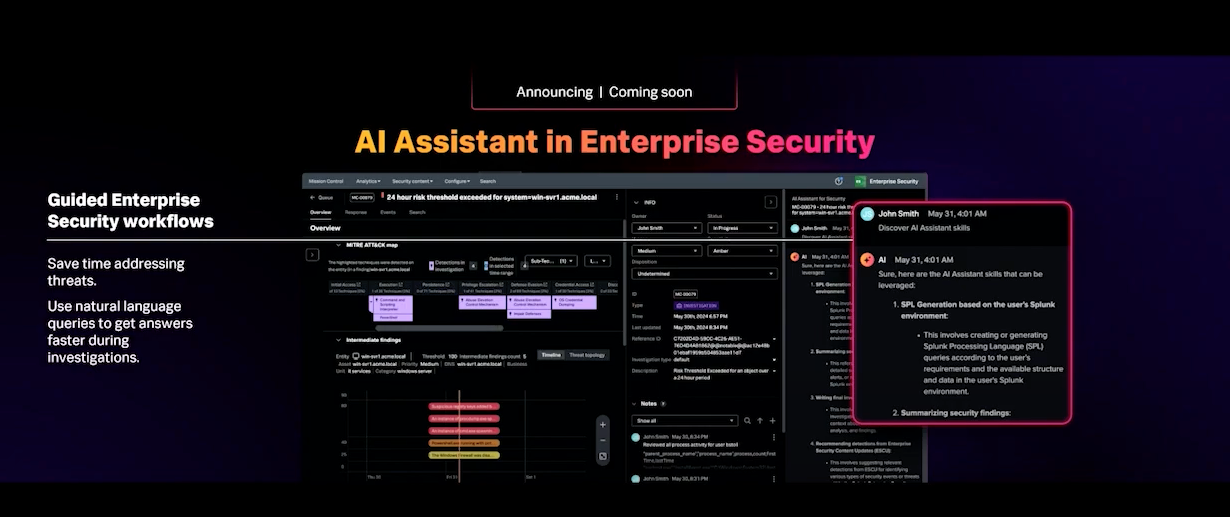
Update Further Reading Nuggets
Observability – new innovations in this space
SOAR 6.3 – external users prompts, especially useful for non SPL users
ES 8.0 is here key highlight is the unified work surface but its emphasis is on MTTR, MTTD and MTTI. A demo is found here at 59 minutes. Its all about bringing together ES as we know it Mission Control, Threat Intel (see Talos above) and SOAR. Talos is “free” for Splunk ES SOAR clients.
Day 2 Wrap Up
Again Day 2 we can see some emerging trends and continual emphasis from Cisco“so our job is not to screw up anything Splunk up”
The focus was very much on integration with many of the Cisco products providing much more data and signals to improve the Splunk experience. Another emphasis was using the extended data with AI through use of assistants and natural language interaction. We like the ingest processor and asset risk and intelligence product.
Splunk have also mentioned repeatedly the need for search, alerts and federation of data outside the platform, something they will have continually to improve upon. There is also a push in joined up security (MTTD, MTTR, MTTI) in one place (Mission Control) with ES 8 to bringing together the components of ES, SOAR and Threat Intel (via Talos which is being bundled free) we would need to further understand free. Certainly a lot going on.
Please stay tuned for daily blog posts from each day of the event between now and the 14th of June. To receive updates directly to your inbox, subscribe here.
-

26 June 2025
SIEM Platform Management
-

26 June 2025
Using Your Data Effectively in Enterprise Security
-

26 June 2025
Data Discovery Process
See how we can build your digital capability,
call us on +44(0)845 226 3351 or send us an email…
