
When managing a growing SIEM platform, staying ahead of threats requires more than just robust defences or the latest features; it demands data and huge amounts of it. The larger the data set and wider and more complex the environment, the more important efficient data management and comprehensive analysis becomes. In this post, we delve into the topic of data pipelining. How it works, how it applies to an effective and responsive SIEM and some of the most widely used tools that facilitate this process.
Intro To Data Pipelining & SIEM
At its core, data pipelining is the process of efficiently transporting, transforming, and enriching data from various sources to its destination, often a SIEM platform. The true value of data pipelining lies in its ability to streamline data flow, reduce log volumes, facilitate multi-destination sending, and enhance the value of logs through faster conversion to metrics and advanced masking capabilities. By optimising data ingestion and processing, organisations can effectively manage security events and mitigate risks in real-time.
Exploring Edge Data
An integral aspect of data pipelining is edge data, generated through edge computing processes. Unlike traditional data processing, edge computing occurs at or near the source of data, providing real-time insights and actions. Edge data, often characterised by limited network bandwidth and decentralised storage, presents unique challenges and opportunities for info security professionals. Harnessing edge data through data pipelining enables organisations to bolster their security posture by extending threat detection and response capabilities “to the edge”.
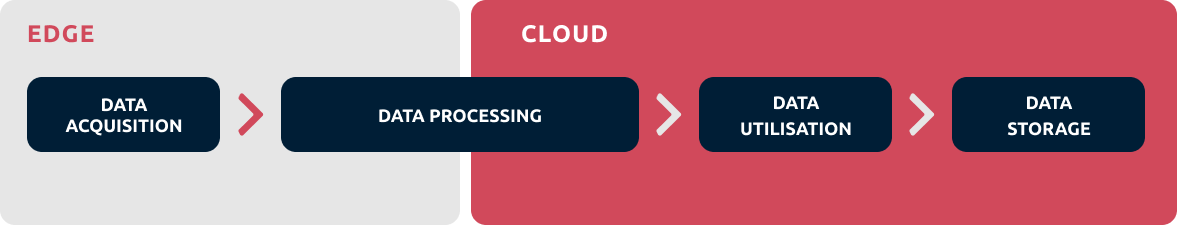
Use Cases for Data Pipelining in SIEM:
Data pipelining finds extensive application across various scenarios. Whether it’s aggregating logs from distributed endpoints, correlating events for threat detection, or enriching data for forensic analysis, data pipelining enhances the efficacy of SIEM functions. Moreover, by optimising data flow and processing, organisations can derive real, actionable insights from diverse data sources, empowering a more proactive threat mitigation and compliance approach.
Key Tools: Cribl Edge and Splunk Edge Processor
Two prominent tools facilitating data pipelining for SIEM are Cribl Edge and the more recently released Splunk Edge Processor.
Cribl Edge is an intelligent, highly scalable edge-based data collection system for logs, metrics, and application data. Crafted in part by former Splunk engineers, it offers an open-source third-party option, enabling organisations to efficiently manage data pipelines with ease.
Splunk Edge Processor, integrated into Splunk Cloud, empowers users with SPL2 language capabilities for seamless data transformation and enrichment in real-time. Edge Processor is designed to help teams optimise their data by reducing noise, improving quality and routing it to the right location.
Both of these tools assist with data management but also optimise resource utilisation, making them useful for reducing high ingestion costs and alert fatigue on most well-established platforms.
Identifying the Need and Prerequisites:
Determining the suitability of data pipelining tools hinges upon various factors, including organisational requirements, infrastructure complexity, and data volume. Before embarking on data pipelining integration, teams should think about having robust network connectivity, a scalable infrastructure, and a clear understanding of the data sources and destinations in their whole business. Only by addressing these prerequisites and doing SIEM discovery work, organisations can maximise the benefits of data pipelining and integration while minimising implementation challenges.
Conclusion and Next Steps:
As organisations face the ever-evolving landscape of more intricate threats, efficient data management and comprehensive analysis through data pipelining has become more important. Key tools like Cribl Edge and Splunk Edge Processor facilitate this process, enabling organisations to streamline data flow, reduce costs, and derive more actionable insights. By addressing these factors, organisations can harness the power of data pipelining to bolster their SIEM platform and stay ahead of emerging threats.
In the next part of this series, we will delve deeper into the specific benefits offered by Cribl Edge and Splunk Edge Processor, how they compare and what should be considered before implementing them.
If you have queries or questions about this topic, please get in touch with one of our SIEM consultants today.
-

26 June 2025
SIEM Platform Management
-

26 June 2025
Using Your Data Effectively in Enterprise Security
-

26 June 2025
Data Discovery Process
See how we can build your digital capability,
call us on +44(0)845 226 3351 or send us an email…
